Protect Your Enterprise From Mobile Attacks
Enterprise-grade, Machine Learning-powered On-device Security
Most Advanced Mobile Threat Defense Solution across the Globe
Enterprise IT organizations are under pressure to deliver a robust mobile experience to employees. One tech publication recently noted that 70% of executives agreed that increasing mobile access to enterprise software represents an immediate digital transformation opportunity.
A market leader in Mobile Threat Defense (MTD) space & offers cutting edge solutions to protect against Mobile Attacks across Device, Network & Application Threat vectors. It helps to make Enterprises work more effectively and efficiently by supporting BYOD programs in an Enterprise & protecting the Mobile Infrastructure which is the new Endpoint today.
It has a proven track record of detecting every major and minor mobile attack over the last 5 years, as attacks happen at machine speed so you need machine speed detection on the device which can be done by us.

zIPS Mobile Device Protection
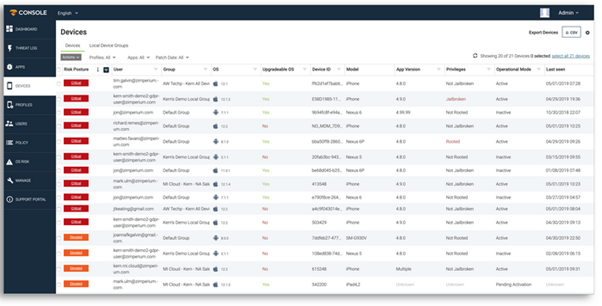
zIPS provides persistent, on-device protection for mobile devices and the information the devices access similar to next generation endpoint protection (EPP) solution’s on traditional endpoints.
- On-device, Machine Learning-based Detection
- Powered By Unparalleled Mobile Threat Research
- Protects Managed & BYOD Devices
Mobile Apps Drive Business and Introduce Risk
Organizations developing mobile apps are keenly aware they need to secure those apps. Mobile apps are increasingly more sophisticated, processing more sensitive personal and corporate information than ever before. An unintentional error in coding could lead to a major security breach
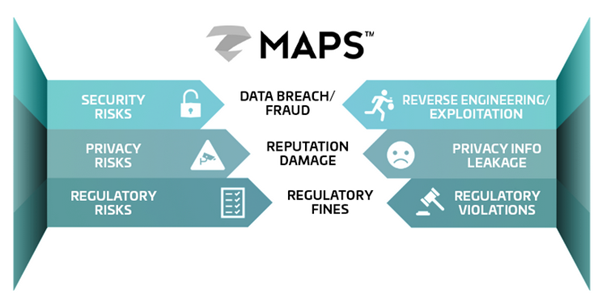
To prevent a breach from occurring, development and security teams need visibility throughout the entire software development life cycle (SDLC). Unfortunately, their efforts have been hindered by a highly fragmented set of app security solutions and no visibility into threats on end-user devices. Zimperium’s Mobile Application Protection Suite (MAPS) addresses both problems so your organization can avoid:
- Data breaches or fraud due to attacks or through reverse engineering;
- Damages to your company’s reputation and bottom line, resulting from private information being leaked; and
- Regulatory fines resulting from not being compliant or because of a breach
The Only Complete Mobile Security Solution
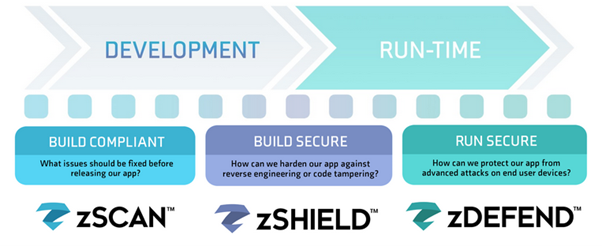
Zimperium’s MAPS identifies security, privacy and compliance risks during app development and protects apps from attacks while in use. Organizations need a consolidated view of all mobile risks during development and continuously after application release. MAPS provides visibility into your mobile development risks and protects apps while in use:
- zScan: Helps your mobile app development organization to discover and fix compliance, privacy, and security issues within the development process before you publicly release your apps;
- zShield: Protects apps with obfuscation and anti-tampering functionality to protect your app from reverse engineering, code tampering and piracy; and
- zDefend: Is an SDK embedded in apps to help detect and defend against device, network, phishing and malware attacks.
z3A Advanced App Analysis

For each risky mobile app that is identified, Zimperium’s z3ATM solution provides deep intelligence, including contextual analysis, as well as privacy and security ratings.
A parallel processing engine continuously collects and correlates data from multiple sources — from malware to data manipulation instances. Multivariate tests and validations are applied so you can identify mobile app security and privacy risks before they become threats. This engine is constantly updated for new threats and the latest app risk behaviors.
You can know in real time what each and every app is doing, including:
- Content: the app code itself
- Intent: the app’s behavior
- Context: the domains, certificates, shared code, network communications.
From a vast and large database of dynamically updated app knowledge, you get detailed quantitative and qualitative intelligence that is tailored to your enterprise’s security and privacy risk management needs.
